Load Balancing Algorithms & Techniques

Stephan Miller
Last updated -
In This Article
If you want to ensure your web service or application runs smoothly under any type of load, you must leverage load balancing. This process distributes traffic across servers so your system runs efficiently and remains accessible regardless of demand.
While this may sound a bit complicated, it’s much simpler than you think once you learn more about it. Luckily, you’re at the right place to discover the best load balancing algorithms and techniques!
So, without further ado, let’s begin.
Understanding Load Balancing
If you’re unsure what load balancing is, here’s a brief explanation to help you understand its purpose and advantages.
It’s a technique for distributing incoming network traffic or workload across multiple servers or resources. Its main goal is to prevent server overload and subsequent performance issues.
Today’s apps handle massive user bases and need to deliver the right content (text, video, images) quickly. To achieve this, most apps leverage data replication, storing the same data on many geographically dispersed servers.
Simply put, a load balancer acts as a traffic director between users and a group of servers. It works by distributing the workload evenly across all available servers.
Most Significant Benefits of Load Balancing
Load balancing manages internet traffic flow between application servers and their users or clients. This helps boost an application’s availability, security, scalability, and performance.
Increased Availability
Thanks to load balancing, you can rest assured that your system will always be available because it distributes traffic across several servers. So, if one of them fails, the traffic will be redirected to other healthy servers, minimizing downtime and ensuring service continuity for users.
Enhanced Scalability
Load balancing provides systems with horizontal scalability by adding more servers to the pool to automatically handle increased traffic or user demands. This prevents bottlenecks that occur when a single server struggles with too much traffic.
Enhanced Security
Load balancing can contribute to app security by helping to mitigate attacks like DDoS, where servers get flooded with requests. They can also monitor incoming traffic to filter out malicious content and reroute attack traffic when combined with firewalls and other security tools.
Improved Performance
Load balancing distributes network traffic across multiple servers, preventing individual servers from overloading. This ensures that users experience consistent and fast response times when accessing applications and services.
Diving into Load Balancing Algorithms
Now that we’ve explored the core principles of load balancing, let’s examine load balancing algorithms and understand their role in optimizing traffic distribution. They are a set of rules used to distribute incoming network traffic across multiple servers evenly, ensuring each request is directed to the most appropriate server.
The use of load balancing algorithms ensures optimal resource utilization and prevents individual servers from becoming overloaded, leading to faster response time and an improved user experience.
Types of Load Balancing Algorithms
There are two main types, each with its own unique approach to distributing incoming client requests evenly among servers.
Static Load Balancing Algorithms
Static load balancing algorithms distribute incoming network traffic (user requests) across multiple servers based on predefined rules and server configurations. They function consistently regardless of the real-time state of the servers.
While easy to implement, they may not be as efficient under fluctuating workloads or server conditions. Common examples include round robin, source IP hash , weighted round robin, randomized algorithm, and URL hash load balancing.
Dynamic Load Balancing Algorithms
The second type of load balancing algorithm adjusts traffic distribution or request routing based on real-time conditions such as server load, network traffic, or resource availability. They continuously monitor the system and require communication between servers and the load balancer.
While this makes them more complex than the static options, dynamic load balancing algorithms ensure that client requests are distributed efficiently. Examples include the least response time method, least connection method, and weighted least connection method.
Load Balancing Techniques Explained
Here are the most common load balancing techniques and how they work.
Round Robin
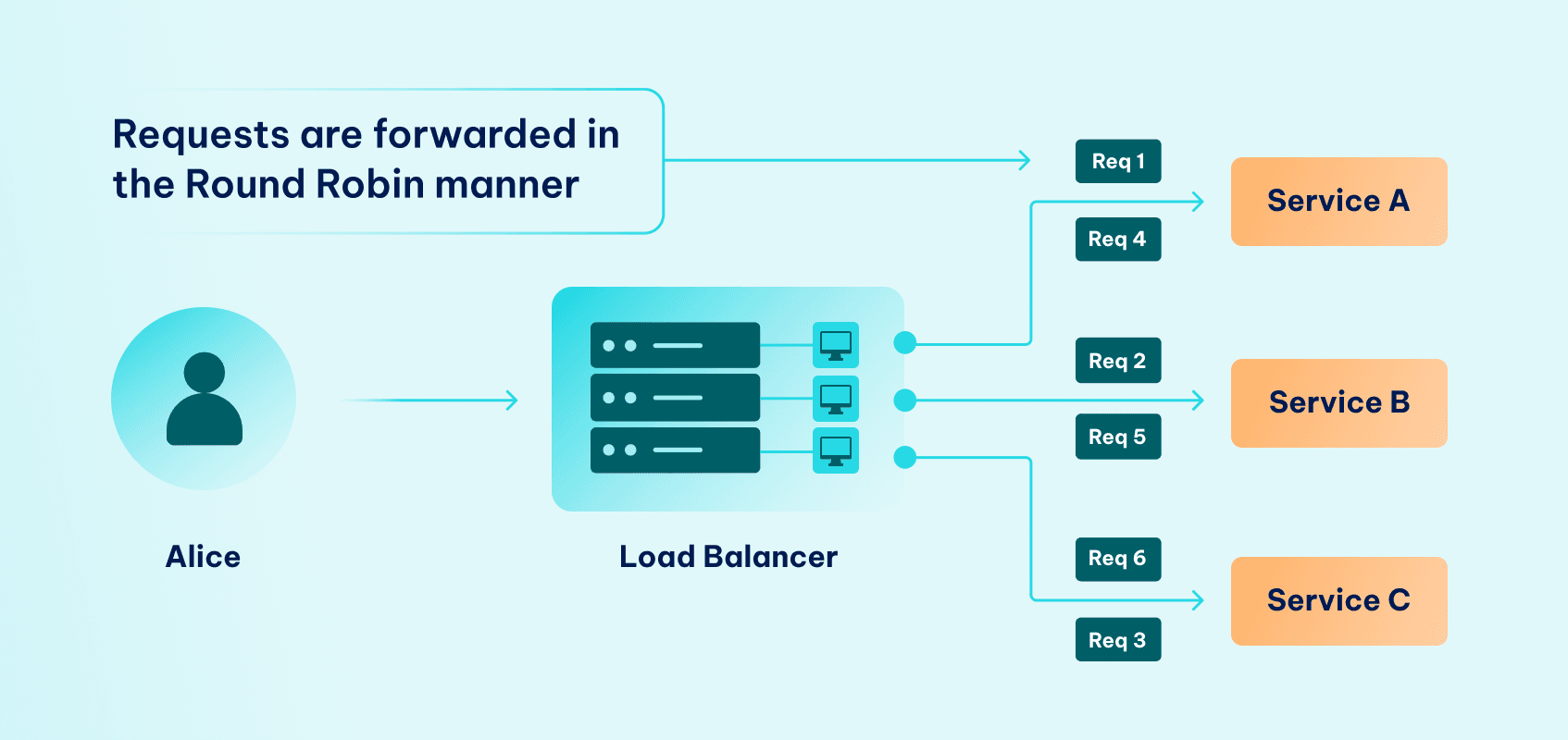
This commonly used algorithm is known for its simplicity. It routes client requests evenly across servers. Basically, the load balancer directs a client request to the first server in the rotating list. Then, it directs each new connection to the next available server in the list.
It’s a simple yet efficient way to ensure no server is overwhelmed. Once all servers in the list have received a connection, the cycle repeats, starting from the beginning.
The round robin algorithm is most effective when handling independent and identically distributed (IID) traffic across servers with similar processing capabilities and resources, like CPU cores and memory configurations). However, it might not be the best choice where servers have varying capacities, or workload distribution is uneven.
Weighted Round Robin
The weighted round robin algorithm is a variation of the round robin algorithm that assigns weights to servers based on their processing power or resource capacity. These weights determine how many connections each server receives in the rotation cycle. Servers with higher weights receive more traffic compared to those with lower weights.
This makes the weighted round robin ideal for scenarios when you want to ensure servers that run business-critical applications get significantly fewer connections than a server delivering static content, preventing the critical servers from overloading.
Least Connections
Least connections is a dynamic load balancing algorithm that prioritizes distributing new active connections to the server with the lowest current load. This approach is particularly beneficial in scenarios involving a significant number of long-lived connections like database sessions.
However, it’s important to note that constantly monitoring and comparing the active connection count on each server can add overhead to the load balancer itself.
Weighted Least Connections
This algorithm builds upon the least connections algorithm by incorporating server “weights” that are assigned beforehand. The load balancer then considers the number of active connections on each server and their assigned weights when making decisions.
Least Response Time
It considers both the number of active connections and the average response time of each server when directing requests. This approach distributes traffic to the server with the lowest current load and the fastest response time.
DNS Load Balancing
This approach, also known as global server load balancing (GSLB), uses the DNS (Domain Name System) to evenly distribute incoming traffic across multiple data servers, usually in different geo-locations. It achieves this by returning different IP addresses from a pool of available servers in response to a single DNS query, directing clients to various servers within the pool.
This load balancing algorithm is simple, but it doesn’t consider the real-time load on the servers, their health status, or the response time of the server.
Source IP Hash Load Balancing
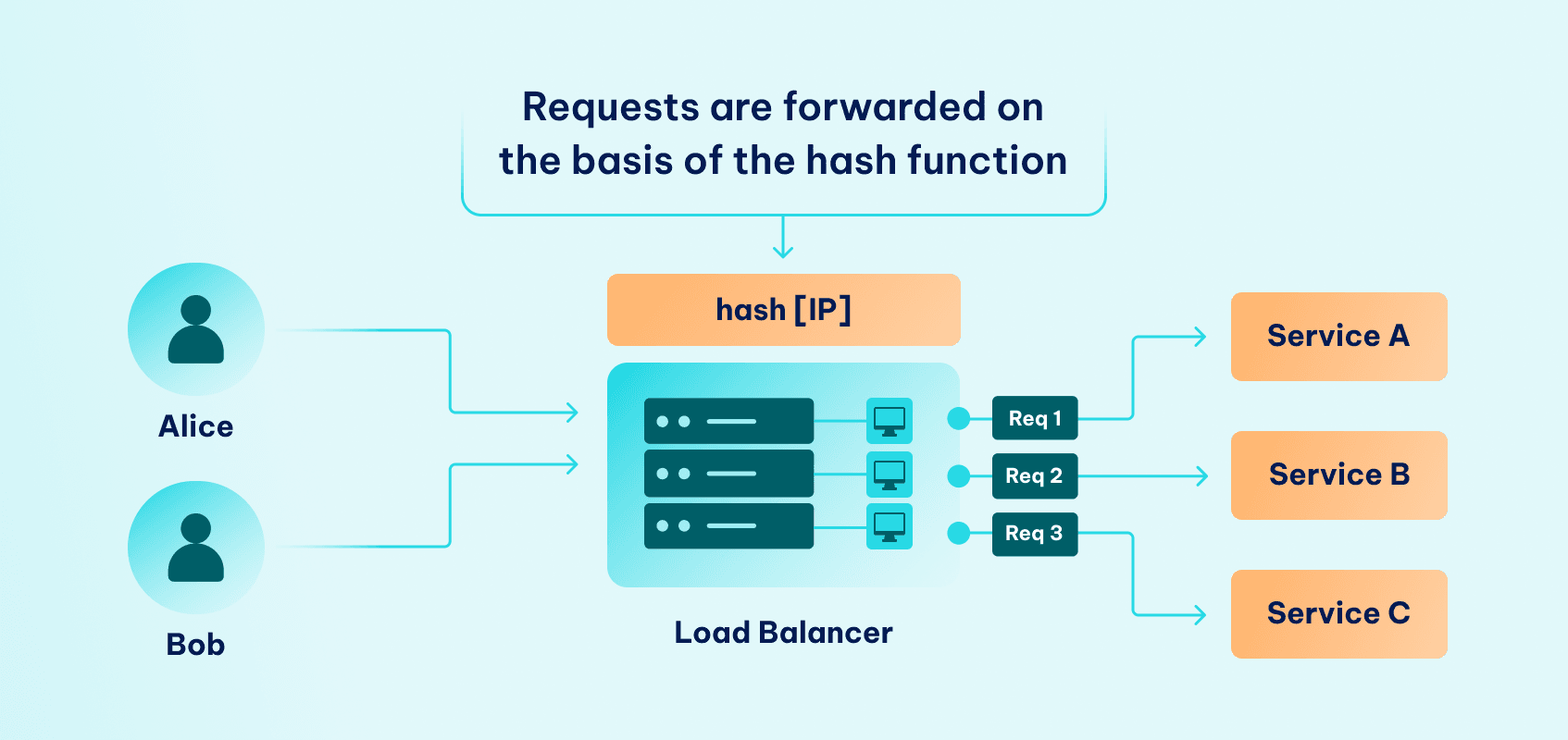
The IP hash load balancing algorithm uses both the destination IP addresses and the source of the client to create a distinctive hash key. This key is used to map the client with a specific server. This key can be regenerated if the session ends, so that following reconnection requests are directed back to the same server.
This method is very useful for maintaining session persistence, ensuring that a client consistently connects to the same server for subsequent requests.
URL Hash Load Balancing
While similar to the source IP hashing, this load balancing method generates a hash based on the URL included in the client request. This approach aims to ensure that all requests targeting the same specific URL are routed to the same server.
Types of Load Balancing Technology
Load balancers can be implemented using either hardware or software solutions.
Hardware load balancers (HLBs) are physical devices specifically designed and optimized for high-performance load balancing. While they can handle significant traffic volumes, their scalability is often limited by their fixed hardware resources. They are also more cost-efficient. If traffic demands exceed the capacity of one HLB, adding another one requires additional investment and deployment.
Software load balancers (SLBs) offer greater flexibility and scalability compared to hardware solutions because they can be installed on existing servers or virtual machines. They are also more compatible with modern cloud computing environments.
Implementing Load Balancing
Setting up a load balancer involves a series of important steps. First, you need to clearly outline the desired objectives for implementing load balancing and select the right load balancer type and algorithm based on factors like traffic volume, scalability needs, fault tolerance, or a combination of these factors.
Next, you need to specify the servers that will participate in the load balancing pool and establish health checks to monitor the responsiveness of your servers.
After the setup, it’s important to keep an eye on a few things. Implement routine maintenance tasks like software updates, system health checks, and security audits to ensure the load balancer’s optimal performance and security. Don’t forget to continuously monitor traffic and performance so you can detect issues early on and make sure your system stays reliable.
Load Balancing Best Practices
Implementing a load balancer effectively requires following best practices to guarantee optimal performance, reliability, and security:
- Thoroughly analyze your application’s requirements and traffic patterns to choose the most suitable load balancing algorithm and configuration.
- When evaluating load balancing algorithms, consider that the load balancer may have capabilities like TLS/SSL encryption offloading or residential proxy services that can improve overall system efficiency.
- Continuously monitor server health and performance metrics like CPU utilization, memory usage, and response times, so you can detect potential bottlenecks or issues early on.
- Ensure proper security measures by protecting your load balancer with strong access controls, enforcing encryption protocols like TLS/SSL to safeguard sensitive data, and conducting regular security audits.
To Sum Up
Effective load balancing plays an important role in ensuring the smooth operation and scalability of websites and applications under varying traffic loads. By understanding the different load balancing methods and their strengths and limitations, as covered in this article, and carefully considering your specific needs, you can select and implement the right solution to optimize performance, reliability, and user experience.

Author
Stephan Miller
Senior Software Engineer
A developer at heart and a communicator by choice, Stephan brings over 20 years of full-stack expertise and five years of mobile development experience to the table. His passion for technology is evident in his published books (Packt Publishing) and insightful articles, both ghostwritten and published under his own name, demonstrating his ability to bridge the gap between technical knowledge and clear communication.
Learn more about Stephan Miller