10 Overlaps And Operational Differences of Data Security vs Data Privacy

Simona Lamsodyte
Last updated -
In This Article
Today’s digital era puts two concepts at the center of data handling and protection discussions: data security and data privacy. While these two ideas can seem intertwined, they each play distinct roles in the wider ecosystem of data protection.
In this article, we will explore the intricacies of the interplay between data privacy and data security.
1. Overlap: A Shared Dedication to Safeguarding Data
The cornerstone of both data security and data privacy is a mutual commitment to data protection. Data security forms a barrier of digital defenses such as firewalls, encryption, and two-factor authentication, aimed at barring unwarranted access to your data. At the same time, data privacy focuses on the ethical and legally compliant use of your data , working to ensure that guidelines and regulations governing data handling are adhered to.
2. Difference: The Protective Approach vs. the End Goal
Where data security and data privacy begin to differ is in their roles within the overall process of data protection. Data security can be seen as the means to an end , establishing the safe passage required to ensure data privacy. This involves preventing data breaches by erecting secure digital defenses. Data privacy then serves as the end goal , stepping in once the passage has been secured. It determines which data ought to be protected and how it should be handled, while adhering to legal and ethical obligations.
Many organizations adopt a zero trust security strategy to bolster the protective approach of data security by continuously verifying and authenticating users and devices, even after gaining access, which aligns with the ultimate end goal of safeguarding data privacy.
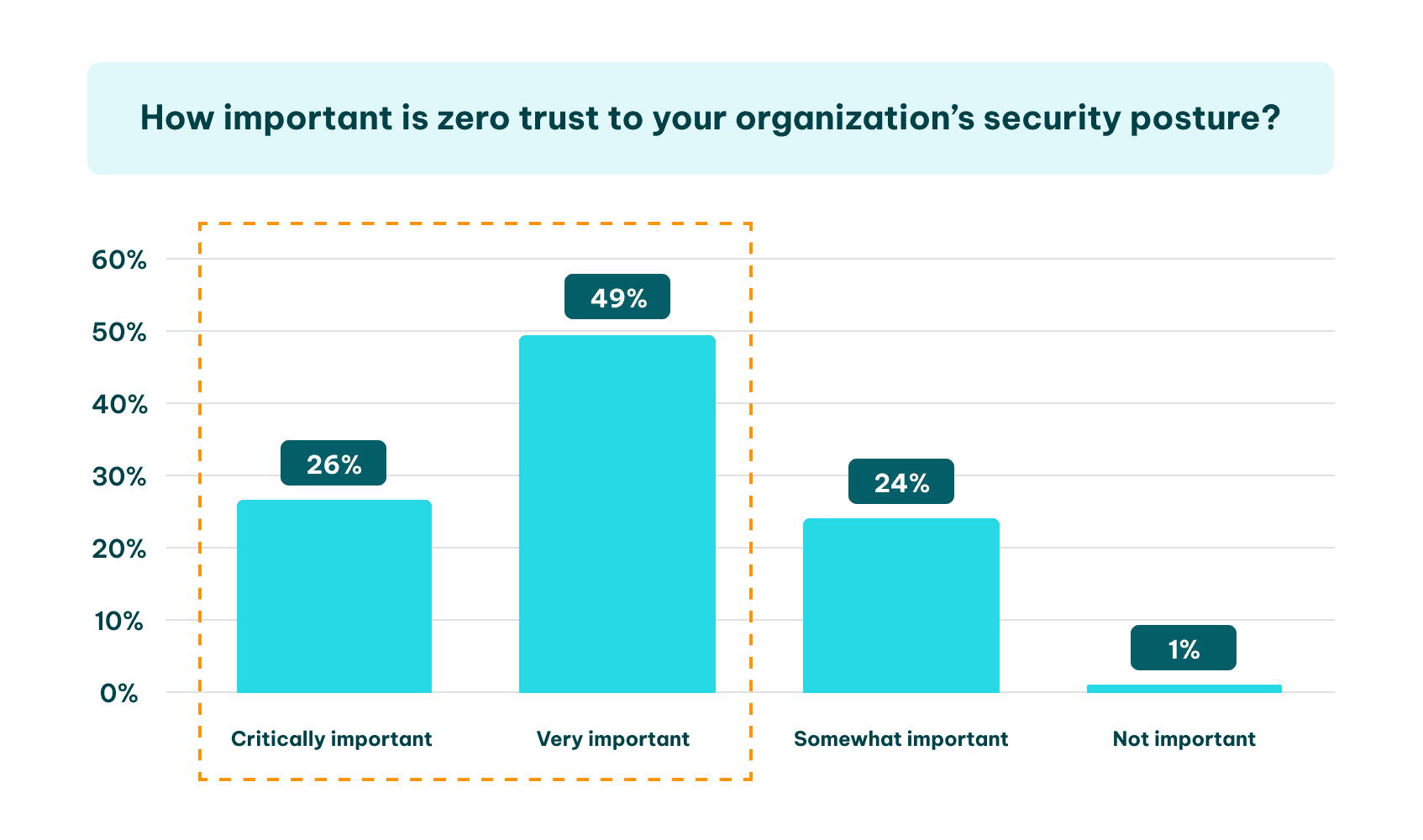 Image sourced from helpnetsecurity.com
Image sourced from helpnetsecurity.com
3. Overlap: Joint Compliance with Legal Standards
One of the key commonalities between data privacy and data security lies in their shared adherence to compliance with legal standards and frameworks. This includes regulatory bodies such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA), as well as frameworks like the NIST cybersecurity framework . These guidelines necessitate a sturdy data security system and provide clear instructions for data handling.
In fact, the NIST framework has become an industry standard in cybersecurity , offering core principles for protecting the confidentiality, integrity, and accessibility of data. This intersection in the legal sphere emphasizes their mutual commitment to complying with legislation and ensuring data protection and privacy.
4. Difference: Handling and Responding to Data Breaches
Data security and data privacy take on different roles when it comes to dealing with data breaches. For instance, as businesses transition from traditional phone systems to cloud PBX software , new security and privacy challenges can arise.
Data security operates proactively, taking measures to prevent breaches from occurring in the first place. This could involve securing communication channels and the data transmitted.
Meanwhile, data privacy typically acts in a reactive manner once a breach has occurred. It dictates the actions required to mitigate the impact, which may include notifying affected parties and appropriate regulatory bodies about any potential breach.
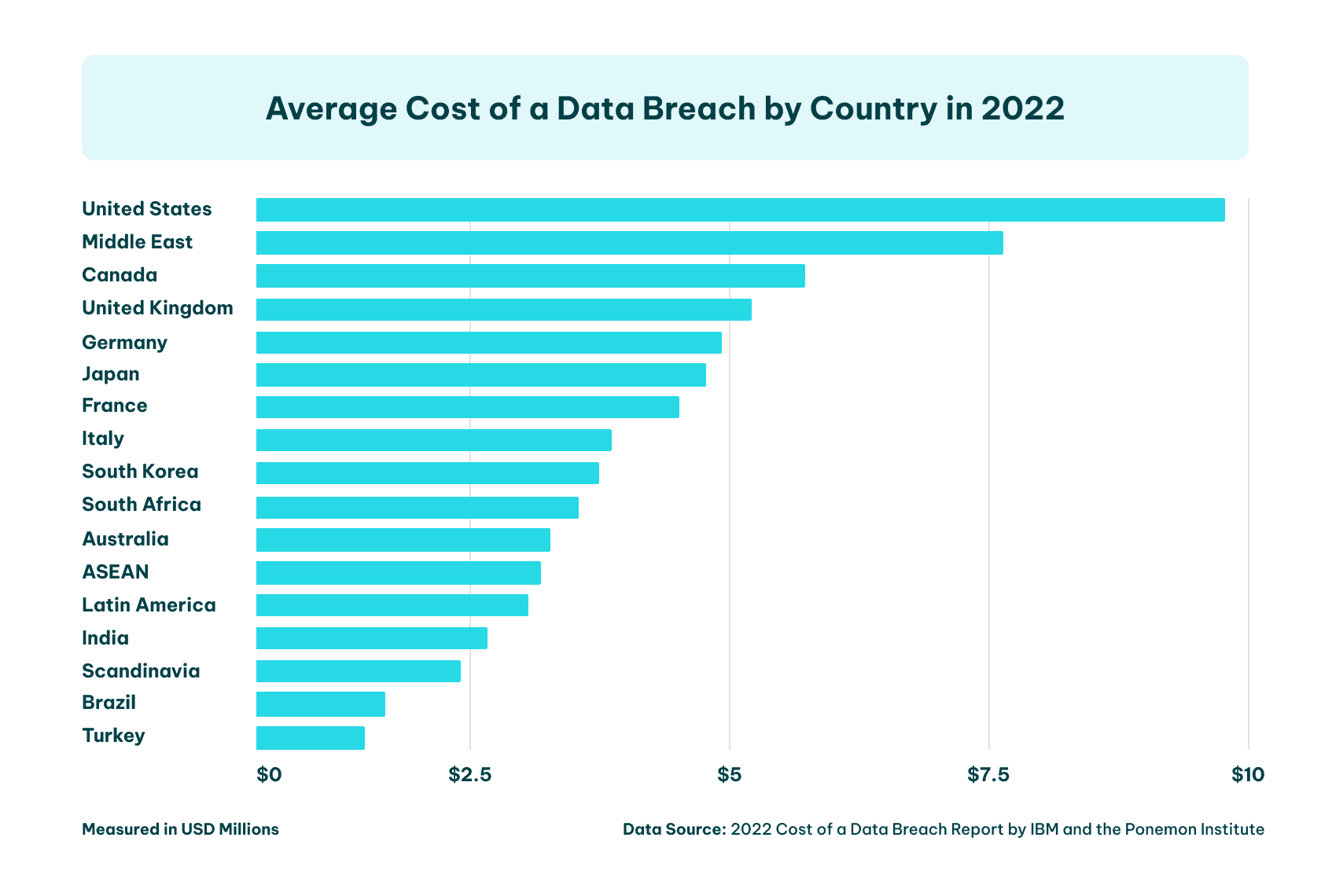 Image sourced from upguard.com
Image sourced from upguard.com
5. Overlap: Unified in Managing Risk
Risk management is a shared concern between data security and data privacy. In the context of data security, a risk assessment plays a vital role. It’s during this risk assessment cybersecurity threats and vulnerabilities are identified, evaluated, and prioritized. However, data privacy requires clear policies in order to safeguard your rights as a data subject and ensure they’re not violated. Together, risk assessments and data privacy policies establish a sturdy structure for handling data-related risks.
6. Difference: The Balancing Act of External and Internal Focus
While data security predominantly guards against external threats, data privacy extends its focus to include internal considerations. It pays close attention to internal processes within an organization to ensure privacy rights are upheld.
This might involve ensuring that access controls are properly implemented, that employees are appropriately trained in data handling, and that any potential privacy issues are quickly identified and addressed.
7. Overlap: The Importance of Ongoing Education
Both data security and data privacy underscore the importance of continuous learning. For instance, if you decide to register .mt domain for your website, understanding how to securely manage this domain and protect the data you collect through it is crucial. As the digital landscape evolves, new risks emerge, and existing ones evolve.
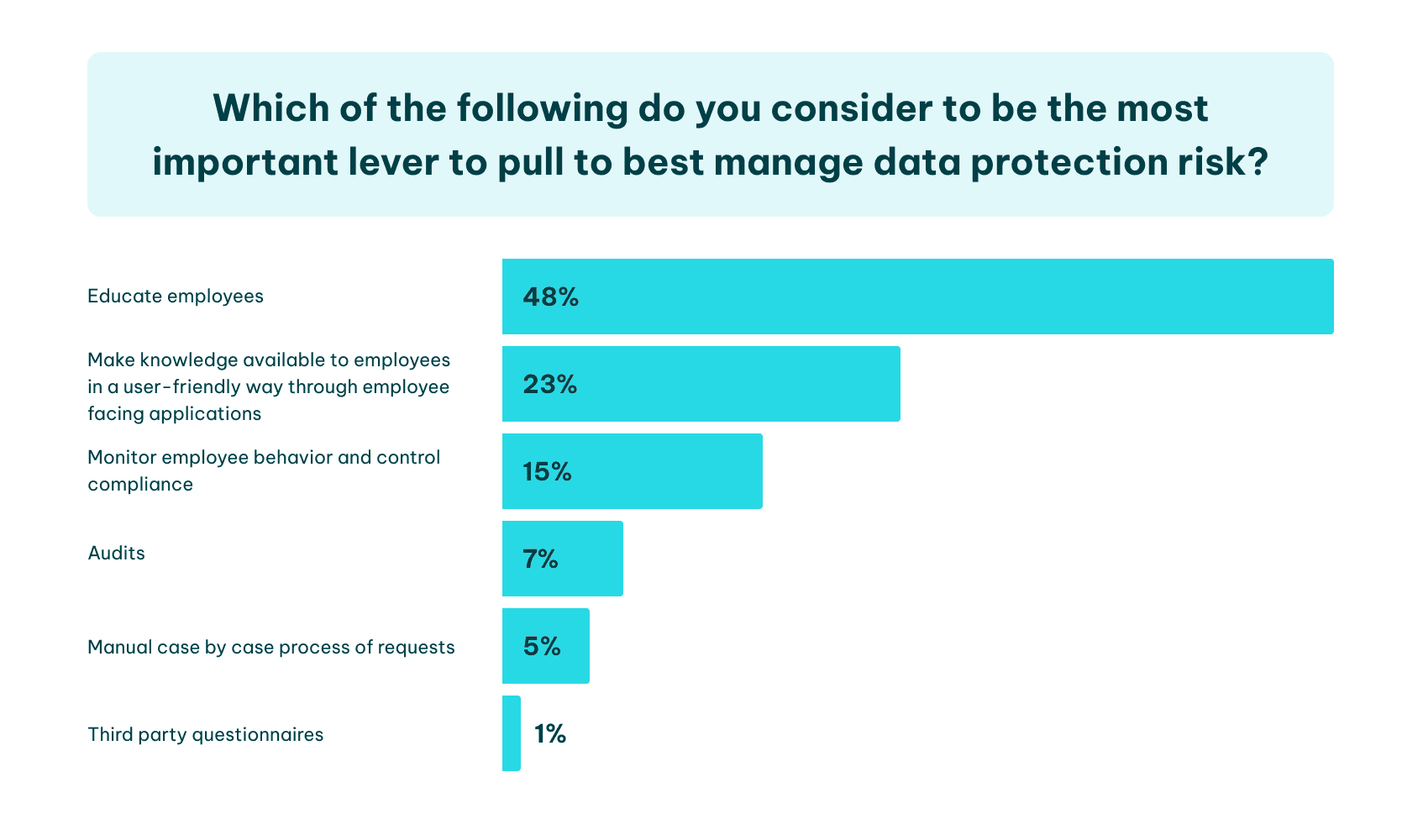 Image sourced from complianceweek.com
Image sourced from complianceweek.com
This necessitates ongoing education about the latest best practices, technological advancements, and regulatory updates , such as understanding the implications of using specific domain registrations. By promoting a culture of learning, organizations can ensure they remain on the cutting edge of data protection and privacy.
8. Difference: Differing Attitudes Towards Data Ownership
Data security emphasizes safeguarding data without addressing ownership directly, whereas data privacy places a strong emphasis on individual consent and control over personal data, highlighting the varying attitudes towards data ownership.
While data security focuses on protecting data regardless of who owns it, data privacy advocates for the rightful ownership and decision-making power to be vested in the individuals to whom the data pertains.
9. Overlap: Necessity of Collaboration
Despite the distinct functions of data security and data privacy, both require an interdisciplinary and collaborative approach. Neither can operate effectively in a silo. The IT, legal, and compliance departments within an organization need to work together to ensure all data security measures align with privacy regulations.
Likewise, privacy officers and legal teams must be knowledgeable about the capabilities and limitations of security technologies to develop effective privacy controls.
10. Difference: The Extent and Focus of Protection
Data security safeguards all data types equally, preventing unauthorized access. On the other hand, data privacy focuses on protecting sensitive personally identifiable information (PII), such as social security numbers and credit card details.
Web scraping , extracting data without consent or compliance, poses a rising threat to data privacy by collecting sensitive information unauthorizedly. Robust data protection measures are vital for maintaining a safe digital environment and ensuring both data security and privacy.
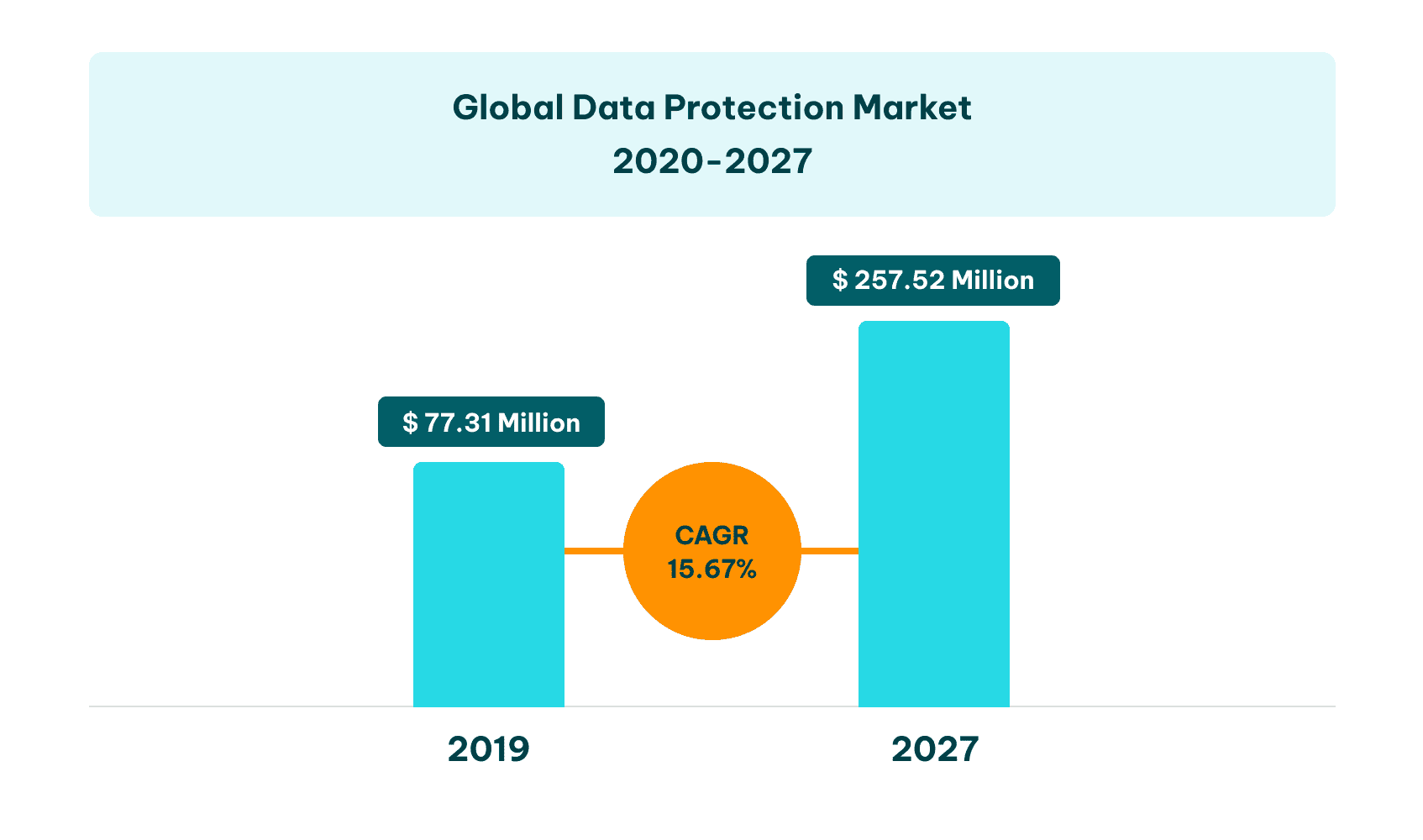 Image sourced from verifiedmarketresearch.co
Image sourced from verifiedmarketresearch.co
Final Thoughts
A nuanced understanding of the overlaps and differences between data security and data privacy allows for more effective navigation of the digital world. This knowledge empowers both individuals and organizations to strike an appropriate balance between data protection and privacy standards.
As we generate and interact with ever-increasing volumes of data, this understanding becomes ever more crucial in creating a safer, more secure, and accountable digital environment.

Author
Simona Lamsodyte
Content Manager
Equally known for her brutal honesty and meticulous planning, Simona has established herself as a true professional with a keen eye for detail. Her experience in project management, social media, and SEO content marketing has helped her constantly deliver outstanding results across various projects. Simona is passionate about the intricacies of technology and cybersecurity, keeping a close eye on proxy advancements and collaborating with other businesses in the industry.
Learn more about Simona Lamsodyte